OSPF LAB
Today I want to show a demonstration on how to create a Network Topology using the following: VLANS | OSPF | ACL
The Goal of this Lab Topology
- Achieve dynamic reachability between all the different subnet on the following network
- I will be using multiple OSPF Areas and have them connect to Area 0 (Backbone)
- Inter-VLAN Routing protocol (Router on a stick)
- Standard Access List (ACL) to make rules for packet flow
This is the network topology I’ve created and we will configure it step by step
Step 1
Configuring PC’s connected to the switches as access ports using the correct VLANS
- I will use the Last usable subnet IP address as the “Default Gateway” for each VLAN
- Notice I have segmented the network for this topology
Configuration
10.0.0.0/26 : Vlan 10
Last usable subnet : 10.0.0.62 : Default gateway
255.255.255.192 /26
10.0.0.64 /26 : Vlan 20
Last usable subnet : 10.0.0.126 : Default Gateway
255.255.255.192 /26
10.0.0.128 /26 : Vlan 30
Last usable subnet : 10.0.0.190 : Default Gateway
255.255.255.192 /26
Lets start the configuration
Configuring PC 1 & 2 (Vlan 10)
Connected to switch 1
IP Address | Default Gateway | both F0/1 - 2 has been assigned as Vlan 10
Configuring PC 3 & 4 (Vlan 30)
Connected to switch 1
IP Address | Default Gateway | both F0/3 - 4 has been assigned as Vlan 30
Configuring PC 5 (Vlan 20)
Connected to switch 2
IP Address | Default Gateway | F0/1 has been assigned as Vlan 20
Configuring PC 6 & 7 (Vlan 10)
Connected to switch 2
IP Address | Default Gateway | F0/2 - 3 has been assigned as Vlan 10
Step 2
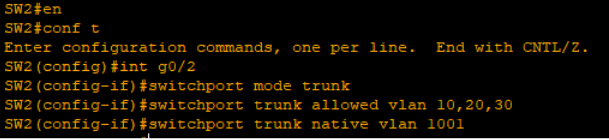
- Now I will trunk the 2 switches together and allow only necessary VLAN to the traffic flow.
- Per rule, I always like to set my native VLAN to an unused VLAN for security purposes
Switch 1
Switch 2
Use the following commands to check Vlan & Trunk Status
“ show vlan brief”
“ show interface trunk”
Notice how for VLAN’s allowed, there is only VLAN 10
This happens because on Switch 2 VLAN 30 was never created
Simply create VLAN 30 to resolve this issue
After you create the VLAN 30
Check “sh int trunk” for update
You should see the following if VLAN 30 was created properly
Before we can configure the Router, we first need to configure g0/2 interface on Switch 2 to allow all 3 VLANS.
This has to be done before we can use the “Router on a stick” to connect Switch 2 to Router 1.
Now we will configure the router to use “Router on a stick” (Inter-Vlan Routing)
Router 1 : G0/0 Interface
Please note that you need to enable the Interface, as cisco router interfaces are disabled by default (Tip)
Now here comes the fun part.
We will apply “sub-interfaces” on R1 G0/0 Interface for individual VLANS.
I personally like to use sub-Interface number to match the VLAN number I am working with.
I will the last usable IP address of the affiliated VLAN subnet
G0/0.10 = Vlan 10
G0/0.20 = Vlan 20
G0/0.30 = Vlan 30
Once this is all done, you now have reachability among VLANS on a different subnet
Step 3
configuring OSPF
IP address for OSPF router 1 |2 | 3 interfaces
Lets first setup the neighboring interfaces with proper IP subnet
Router 1
Router 2
Router 3
After all the Interfaces has been configured, its time for OSPF Configurations
- I will first be configuring Area 0 backbone OSPF for router 1 | 2 | 3
- Create Loopback IP Address (Always stays up/up State)
- Apply OSPF config for individual Interfaces
Please Note that there are variety of method of applying OSPF config
This method of OSPF is rather simple, as it does not require an individual interface IP address to be considered OSPF.
By having 10.0.0.0 0.0.255.255 area 0 = This means as long as the first 2 octet is 10.0 -> it will automatically enable that IP subnets into OSPF Area 0
Router 1 (Area 0)
Interface g0/1 - 2
Router 1 (Area 3)
Interface g0/0
Router 2 (Area 0)
Interface g0/0 - 1
Router 2 (Area 1)
Interface g0/2
Lets configure Server 0 that is connected to R2 (Area 1)
IP Address | Subnet Mask | Default Gateway of the nearest router Interface
Router 3 (Area 0)
Interface g0/0 - 1
Router 3 (Area 2)
Interface g0/2
Lets configure Server 1 that is connected to R3 (Area 2)
IP Address | Subnet Mask | Default Gateway of the nearest router Interface
Finally, once all the configuration has been properly configured, we should have full dynamic reachability between the pc’s and the servers
- Lets do a ping test for confirmation
Ping Test : Successful
Step 4
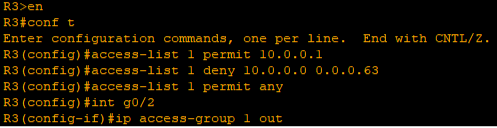
Lastly, I want to add a simple standard ACL rule to this network topology
Rule being applied :
- I only want PC 1 from the subnet “10.0.0.0 /26” to be able to reach Server 1
- All other PC’s within the same subnet cannot access server 1
Following is the command I will execute:
access-list 1 permit 10.0.0.1
access-list 1 deny 10.0.0.0 0.0.0.63
access-list 1 permit any
interface g0/2
ip access-group 1 out
Now the fun part… lets ping and see if the rule got applied
As previously stated, PC 1 should be able to ping Server 1
Successful, PC 1 was able to ping server 1
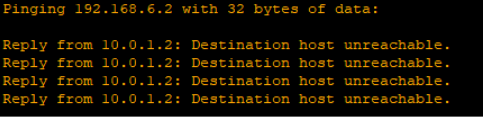
- Finally, lets see if the other PC’s in the same subnet can ping the server 1
- Note that, it has to fail sending the ping to verify that our configuration worked as intended
Successful, PC 2 was not able to ping server 1 despite being in the same subnet.
This means our ACL rule has successfully taken into effect.
I showed a demonstration on how to setup a Lab topology using ACL | VLANS | OSPF.
I hope you enjoyed it
Thank you
- Chris